In today’s digital world, cybersecurity and compliance are more critical than ever—and for good reason. Entrusting companies with personal or private data feels increasingly risky as data breaches frequent news headlines. While there are policies like SOC 2 in place that are meant to protect consumer information, data privacy is primarily a matter of corporate adherence to regulations. So, what is SOC 2 compliance?

What Is SOC 2?
SOC 2, or Systems and Organization Controls 2, is a standardized cybersecurity compliance framework that helps organizations protect customer data and reduce the risk of security breaches. It includes a comprehensive set of criteria that is meant to ensure effective information security, covering everything from company management and employee onboarding to third-party communications and risk management.
SOC 2 Trust Services Criteria
SOC 2 compliance is based on five Trust Service Criteria (TSC):
- Security: Ensures that the system is protected against unauthorized access, both physical and logical.
- Availability: Ensures the system is available for operation and use as committed or agreed.
- Processing Integrity: Ensures that system processing is complete, valid, accurate, timely, and authorized.
- Confidentiality: Ensures that information designated as confidential is protected as committed or agreed.
- Privacy: Ensures that personal information is collected, used, retained, disclosed, and disposed of in conformity with the commitments in the entity’s privacy notice.

SOC 2 Components
- Policies and Procedures: Developing and documenting policies and procedures that align with the Trust Service Criteria.
- Risk Assessment: Identifying and assessing risks related to the security, availability, processing integrity, confidentiality, and privacy of the system.
- Controls: Implementing controls to mitigate identified risks, which include both preventive and detective controls.
- Monitoring: Continuously monitoring the system and controls to ensure they are functioning effectively and efficiently.
- Audit and Reporting: Undergoing regular audits by an independent third-party auditor who evaluates the controls and provides a SOC 2 report.
SOC 2 Type 1 vs. Type 2
The name “SOC 2” suggests the existence of SOC 1, and indeed, there are various SOC compliance reports that assess risk differently. SOC 2 Type 1 and SOC 2 Type 2 are both reports that require an independent auditor to assess your cybersecurity controls against a set of criteria. They differ from each other when it comes to scope, the timing and cost it takes to conduct the audit, and ultimately the value to your clients or customers.
SOC 2 Type 1 is an attestation report that assesses an organization’s cybersecurity controls at a single point in time. It helps determine whether the systems put in place to protect data and information from attacks are designed effectively. SOC 2 Type 1 is different from SOC 2 Type 2, which assesses the effectiveness of those cybersecurity controls over time. While there is no required time period for a SOC 2 Type 2 audit, most organizations will use a 6-month audit period.
SOC 2 Type 1 audits are typically less expensive and time-consuming to conduct than Type 2 audits. However, they are an important step towards achieving a SOC 2 Type 2 audit.
Why is it important to work with companies that are SOC 2 compliant?
SOC 2 compliance is meant to assure customers that companies have taken sufficient measures to protect their data. By working with a SOC 2-compliant company, customers can reduce their own risk of data breaches and can trust that the company they’re working with has been legitimately and independently audited. However, the benefits of working with SOC 2 companies extend beyond peace of mind that your data is protected.
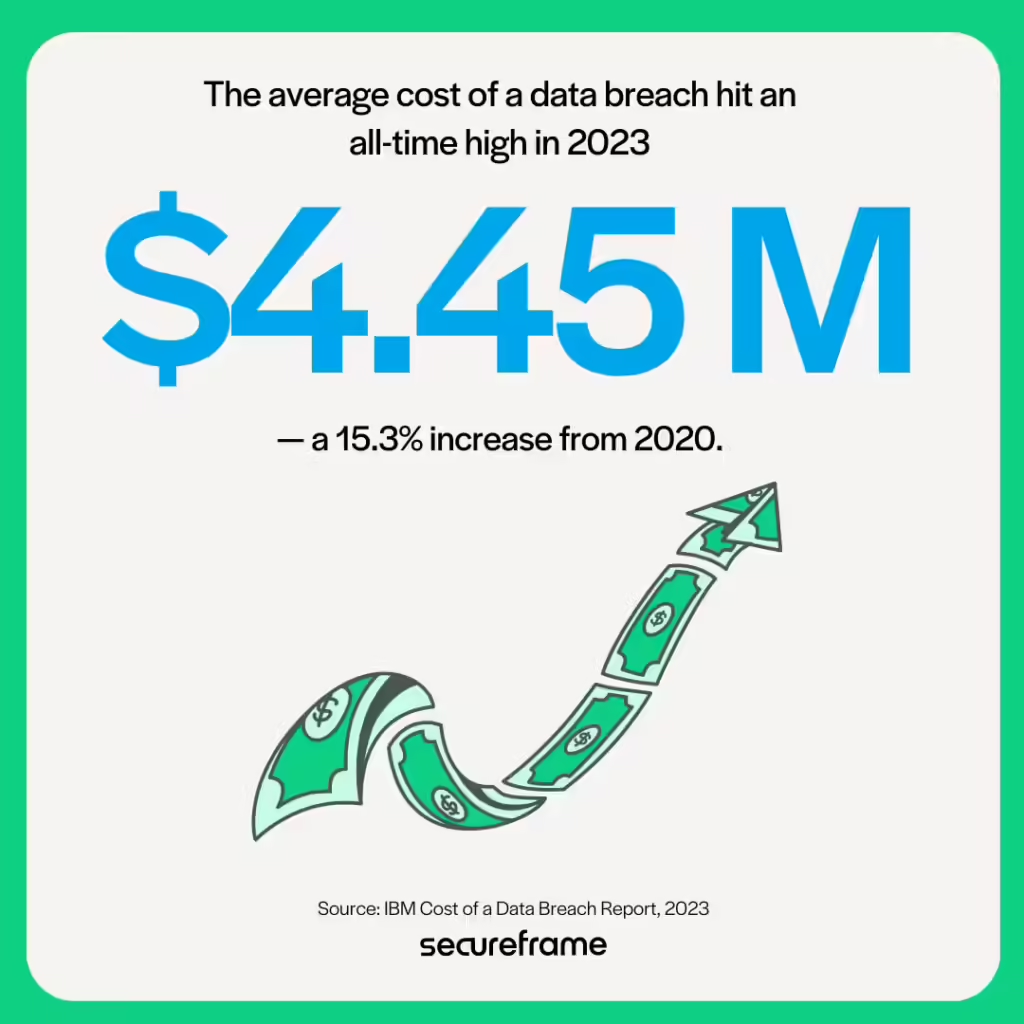
SOC 2 transparency standards enable customers to get clear and easy insight into how their data is being managed and protected. It also comes with regulatory benefits for customers who are undergoing their own audits. Customers can demonstrate their own compliance during audits by showing they work with SOC 2-compliant vendors.
Choosing Trusted SOC 2 Vendors
Cybersecurity should be a top concern for any company that handles customer data and information. SOC 2 standards are an effective way to not only ensure that your security systems are sufficient for protecting your customer data but also to help build trust with your customers.
TrueLook is proud to announce that we have achieved SOC 2 Type II compliance. At TrueLook, we are dedicated to upholding the highest standards of security and compliance, so that our customers don’t have to worry about their data.

For a company handling remote live viewing and construction time-lapse videos, SOC 2 compliance is crucial. It ensures data security, builds trust and credibility, meets regulatory requirements, maintains operational integrity, protects confidentiality and privacy, and supports effective risk management.
Want to learn more about what TrueLook is doing to safeguard our data?
See our comprehensive progress report that documents our compliance against global standards including certifications, attestations, and audits.

